Harbor – Authentication OIDC with VMware Workspace ONE Access

In this post I will go through how you can configure Harbor by VMware to be setup with a OIDC Provider to be able to provide SSO (Single Sign On) utilizing VMware Workspace ONE Access.
First off it is necessary to have both Harbor and VMware Workspace One Access in place.
VMware Workspace One Access supports OpenID Connect or OIDC. This is used to be able to provide SSO access for login and utilizing Role Based Access Control inside of Harbor for different Projects and Repositories that Developers need to utilize inorder to upload Helm charts and Container Images.
By utilizing VMware Workspace One Access we can also make sure that administrators and developers that need access to other services for example NSX-T or Cloud Director.
Create the Harbor Web Application
Content
- Login to Workspace One as the local administrator
- In the Workspace One Administrator Console head over to the Catalog/Web Apps and create a New Application
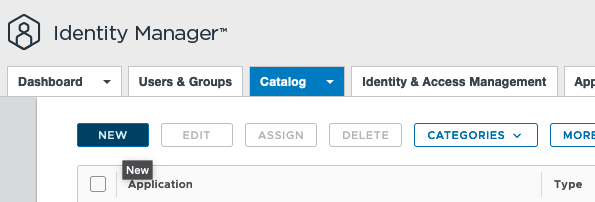
3. Provide a Name and upload a Logo for the Harbor Application
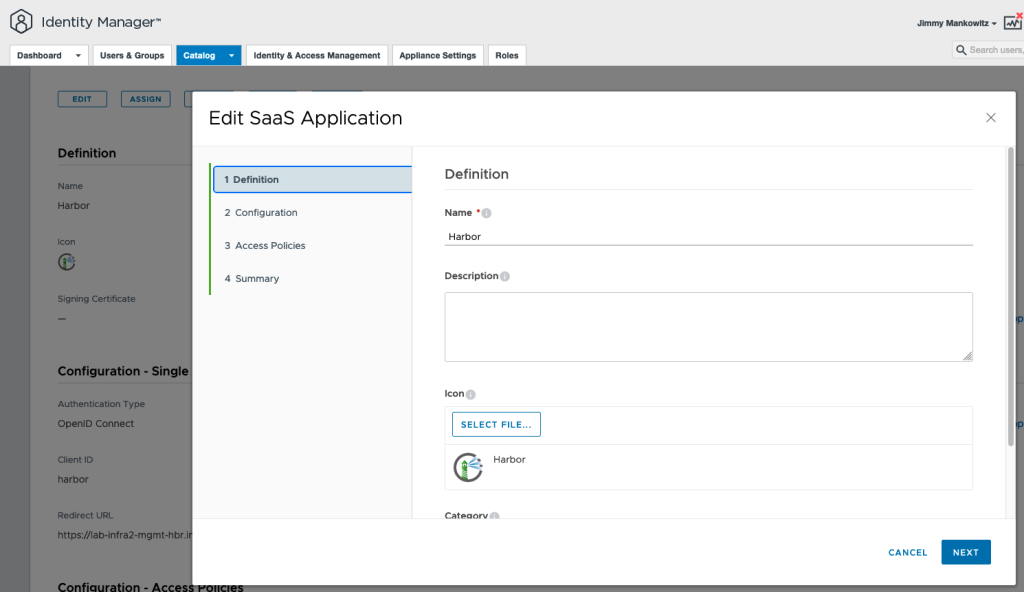
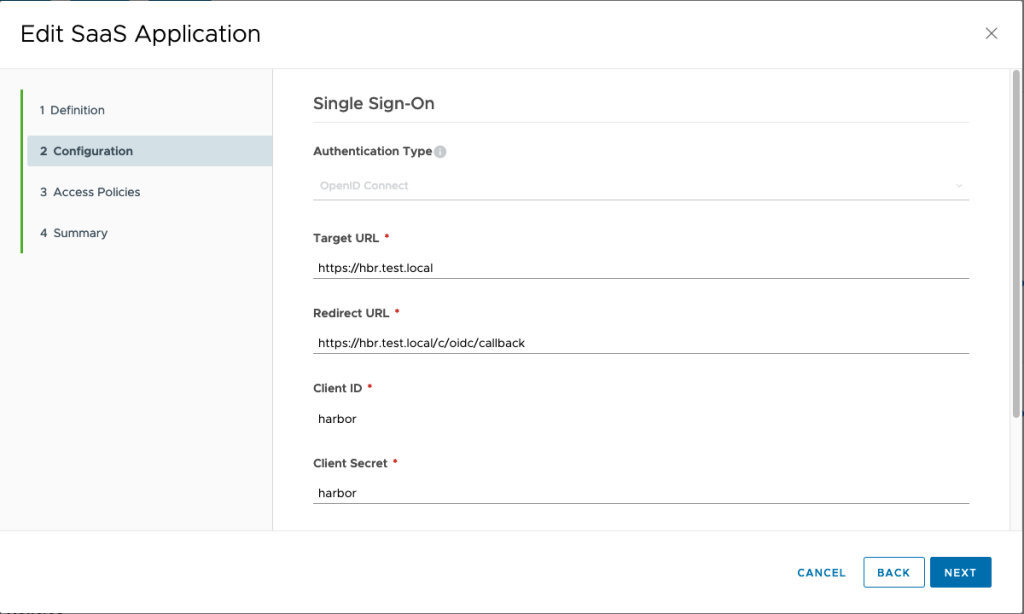
4. On the next screen add the Harbor Target URL as-well as the Redirect URL
Usually this is https://harbor_address/c/oidc/callback
This can be found during the configuration of the OIDC in the Harbor UI as seen below.
5. Next screen is where we save the configuration.
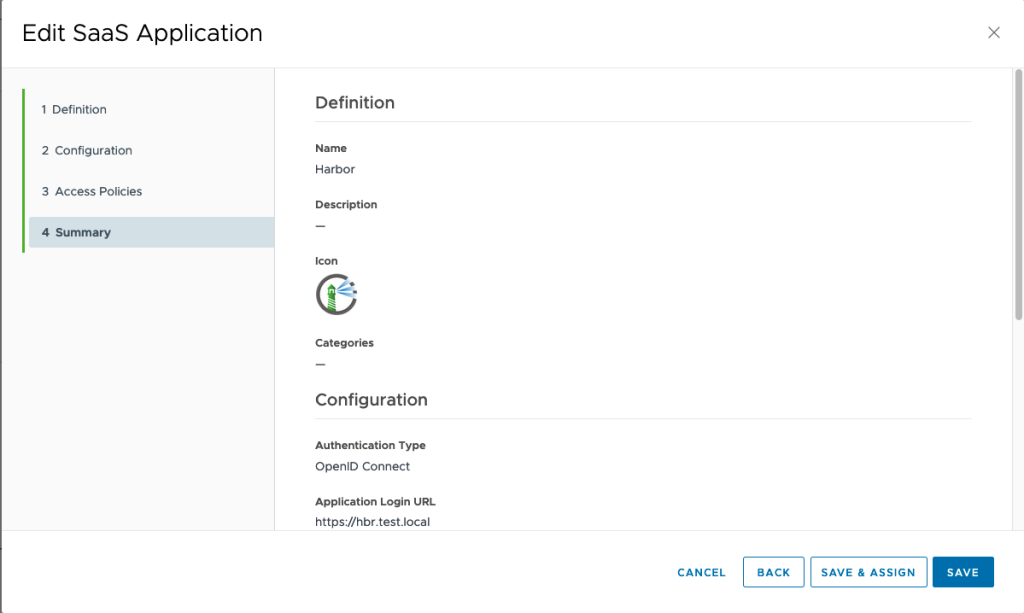
Configure the Harbor OIDC connection
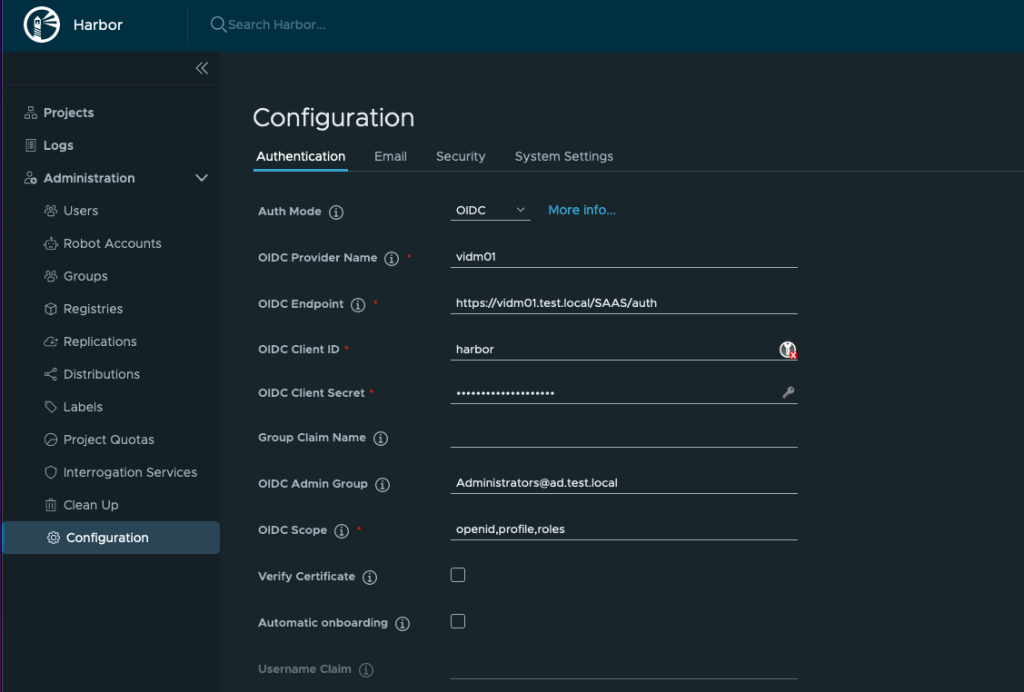
6. Now we head over to the Harbor UI to configure the OIDC connection.
login as admin and go to configuration.
Select Auth ode OIDC and then enter:
OIDC Provider Name: The Name of the Workspace One Access machine
OIDC Endpoint: https://The Workspace One Access URL followed by: /SAAS/auth
OIDC Client ID: harbor
OIDC Client Secret: harbor
OIDC Admin Group: The Active Directory Administrator Group that has been added In WOA to be admin
OIDC Scope: openid,profile,roles
- OIDC Provider Name: The name of the OIDC provider.
- OIDC Provider Endpoint: The URL of the endpoint of the OIDC provider.
- OIDC Client ID: The client ID with which Harbor is registered as client application with the OIDC provider.
- OIDC Client Secret: The secret for the Harbor client application.
- OIDC Group Filter: The regular expression to filter OIDC groups.Only the groups that match the provided regular express will be added to Harbor.
- Group Claim Name: The name of a custom group claim that you have configured in your OIDC provider, that includes the groups to add to Harbor.
- OIDC Admin Group: The name of the admin group, if the ID token of the user shows that he is a member of this group, the user will have admin privilege in Harbor. Note: You can only set one Admin Group. Please also make sure the value in this field matches the value of group item in ID token.
- OIDC Scope: A comma-separated string listing the scopes to be used during authentication.

Testing Harbor SSO Login with OpenID Connect
Now given that we have an Active Directory user added to the Administrators group we should be able to login to Harbor with that user.
We can see the botton Login via OIDC provider in the UI.
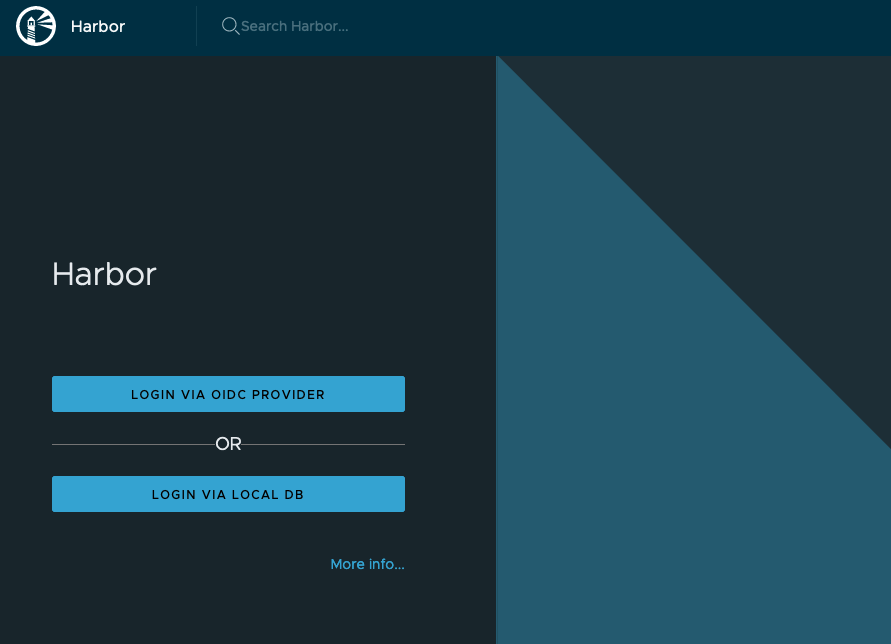
When we press it we should be redirected to the Workspace One Access SSO page and select the domain to be able to login as our user.


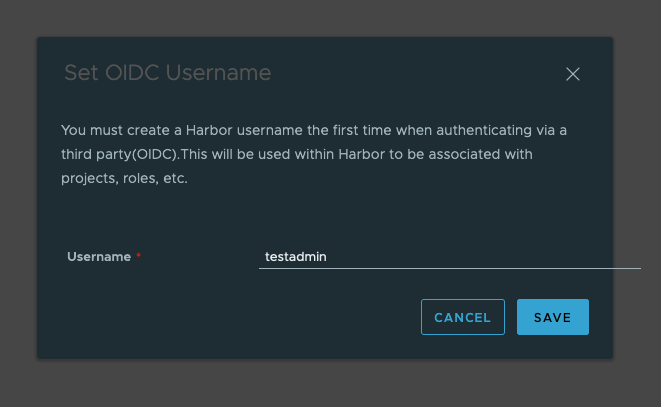
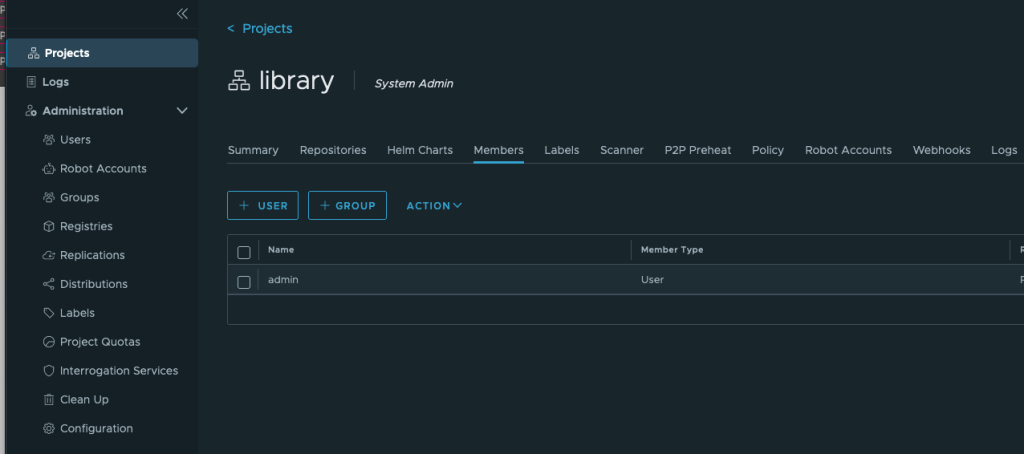
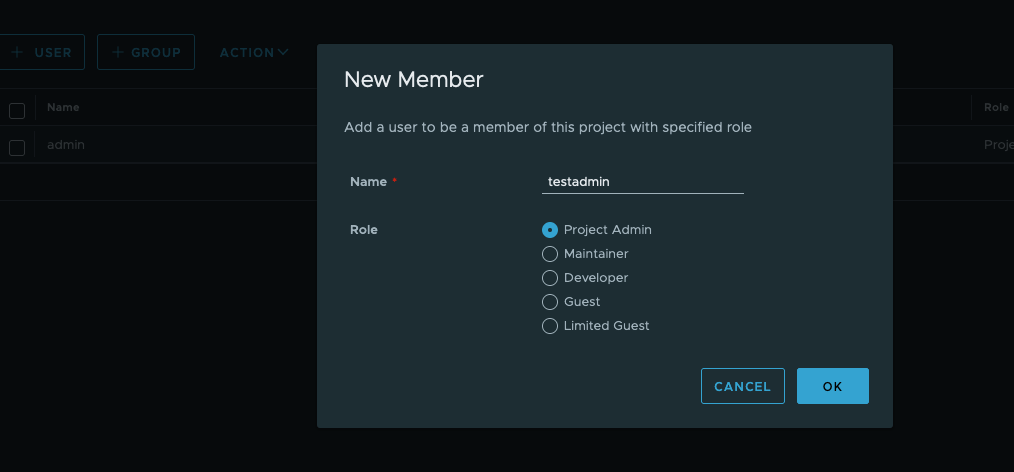
The first time the user login it need to provide a name in Habor to be used.
Using OIDC from the Docker/Kubernetes/Tanzu or Helm CLI
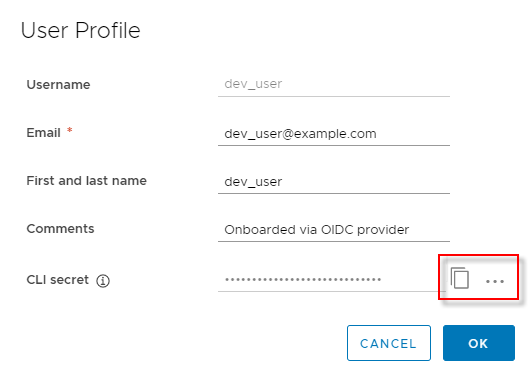
If you wish to utilize the the user you just created to be able to upload Images or Helm charts into Harbor you can find a CLI secret for the user that was just created.
After you have authenticated via OIDC and logged into the Harbor interface for the first time, you can use the Docker or Helm CLI to access Harbor.
The Docker and Helm CLIs cannot handle redirection for OIDC, so Harbor provides a CLI secret for use when logging in from Docker or Helm. This is only available when Harbor uses OIDC authentication.
- Log in to Harbor with an OIDC user account.
- Click your username at the top of the screen and select User Profile.
docker login -u testadmin -p cli_secret hbr-test.local
Note: The CLI secret is associated with the OIDC ID token. Harbor will try to refresh the token, so the CLI secret will be valid after the ID token expires. However, if the OIDC Provider does not provide a refresh token or the refresh fails, the CLI secret becomes invalid. In this case, log out and log back in to Harbor via your OIDC provider so that Harbor can get a new ID token. The CLI secret will then work again.


0 Comments